Introduction
DDoS (Distributed Denial-of-Service) attacks are among the most common server security threats with a steady year-over-year increase in the attack frequency and strength. While server owners rarely anticipate DDoS-related threats, the attacks can be mitigated by monitoring resources and acting promptly.
This article will show you how to check your Linux server for DDoS attacks and offer quick response tips.

What Is a DDoS Attack?
A DDoS is an attack in which a malicious actor exhausts all the available server resources by overwhelming the network with requests. Unlike the standard DoS (Denial of Service) attack, DDoS:
- Employs multiple distributed devices, usually owned by unwitting people whose equipment was hacked.
- Targets multiple network devices and protocols, not just the network endpoints.
Below are the three main types of DDoS attacks.
- Application layer DDoS (Layer 7 attack). Focuses on the software powering the server, such as Apache and Nginx web servers. This DDoS type is the most common.
- Protocol DDoS. Targets OSs and firewalls on essential network devices.
- Volumetric DDoS. Generates an overwhelming amount of traffic to consume the available server bandwidth and throughput.
How To Check for a DDoS Attack on a Linux Server?
Malicious actors use standard network paths to conduct DDoS attacks. Therefore, detecting attacks by monitoring your network traffic for unusual connections is often simple. The following sections list the simplest ways to check if your server is experiencing a DDoS attack.
Check Server Load
Check the server's average load with the uptime command:
uptimeThe three values displayed under load average represent the average load over one minute, five minutes, and fifteen minutes, respectively.
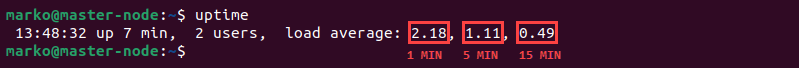
A handy reference number for the acceptable server load is the number of threads available on a server. A load that equals or is bigger than the number of threads may suggest a suspiciously high activity.
Enter the following command to check the number of threads available on your server:
grep processor /proc/cpuinfo | wc -l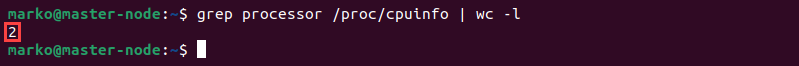
In this example, the server has 2 available threads. An average load higher than 2 points to an unusually high server load.
Check Network Load
If your server is slow but remains accessible over a direct connection (e.g., via IPMI), use one of the tools below to inspect the load of your network.
Note: To install any of the utilities below, use your distribution's package management system. For example, use APT on Debian-based systems:
sudo apt install [name-of-the-utility]
bmon
bmon is a bandwidth monitor and rate estimator designed to be user-friendly and provide simple data visualization in a text-based environment.
To start bmon, type:
bmonNavigate to the interface you want to inspect with the up or down arrow keys on your keyboard.
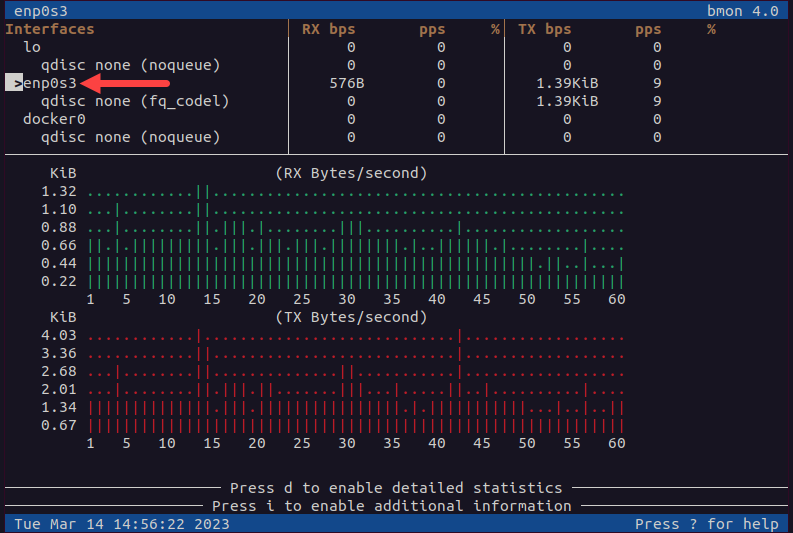
bmon presents real-time information in multiple categories. Browse through the categories by pressing the left or right arrow key.
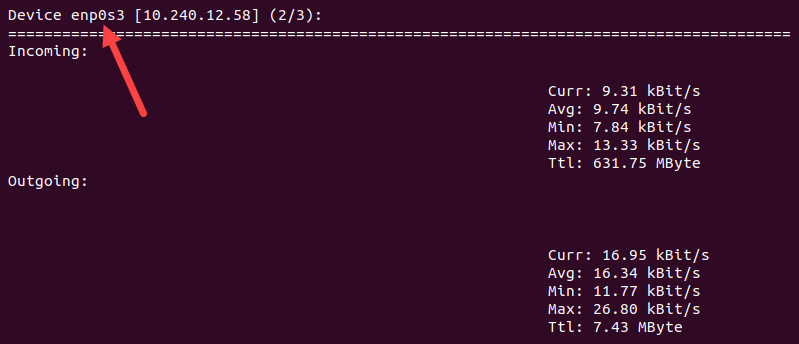
nload
The nload utility helps monitor network traffic and bandwidth usage in real-time. Start nload by typing:
nloadPress the left or right arrow key to navigate to the interface you want to monitor. The utility displays incoming and outgoing network traffic details for the chosen interface.
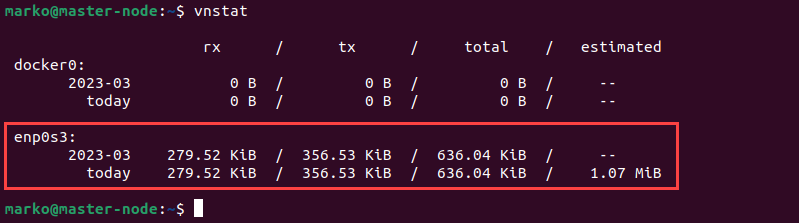
vnStat
Like nload, vnStat is a traffic monitoring utility. The benefit of vnStat is that it keeps hourly, daily, and monthly network traffic logs for the given interface.
Access vnStat by typing:
vnstatThe utility lists all the available interfaces by default.
iftop
The iftop utility displays a list of network connections and the related network information in a user-friendly format. By default, the list is organized according to bandwidth usage.
Start iftop with the following command:
iftop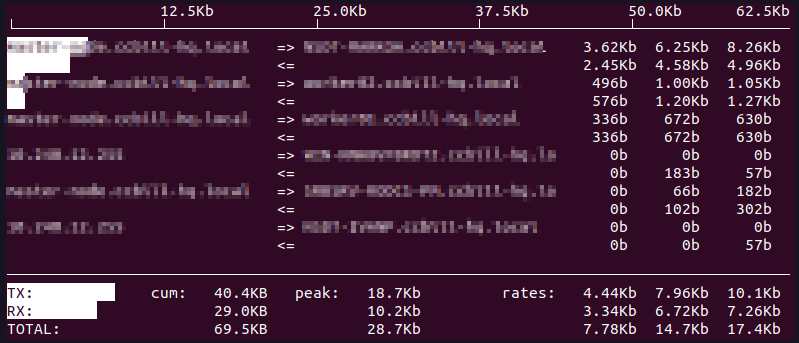
ifstat
The ifstat command outputs network interface statistics. By default, it displays incoming and outgoing network traffic data for each active interface. Access ifstat by typing:
ifstat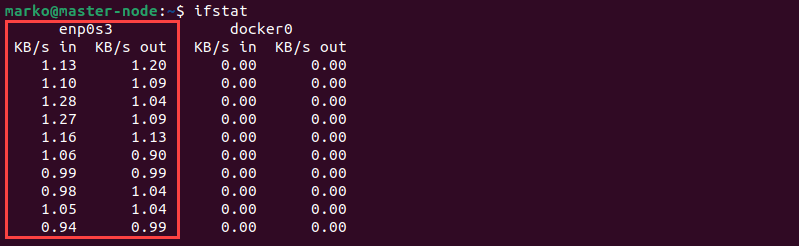
Check What IP Addresses Are Connected to Server
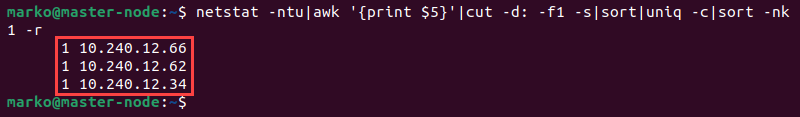
Listing the IP addresses of the devices currently connected to your server may help you identify potential threats. The netstat command is a utility that provides an overview of network activity, including information about the connections.
The command below uses netstat with the -n, -t, and -u options to create an output that contains numerical addresses of the TCP and UDP connections. The output is then formatted using the awk, cut, and sort commands.
netstat -ntu|awk '{print $5}'|cut -d: -f1 -s|sort|uniq -c|sort -nk1 -rThe final output displays the number of active connections for each connected IP address.
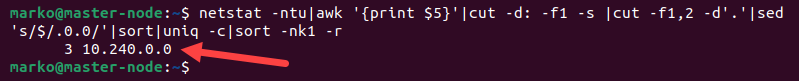
On busy servers, the list may be very long and difficult to read. You can filter the output to show all the connections in the same subnet on one line. The following example combines the IP addresses in the same 255.255.0.0 subnet mask.
netstat -ntu|awk '{print $5}'|cut -d: -f1 -s |cut -f1,2 -d'.'|sed 's/$/.0.0/'|sort|uniq -c|sort -nk1 -rThe output now shows only one line. The number 3 before 10.240.0.0 suggests three connections come from that IP address.
How to Mitigate a DDoS Attack on a Linux Server?
Once you confirm that a DDoS attack is happening on the server, a few quick actions may mitigate the damage.
Note: Unprotected servers quickly become victims of DDoS attacks. A dedicated server with DDoS protection is prepared to continue working without disruptions in availability.
Use the route command to block the attacker's IP address.
sudo route add [ip-address] rejectNote: The route command is part of the net-tools package. To install it on Ubuntu, type:
sudo apt install net-tools
Alternatively, use the iptables firewall:
1. Block access to an IP address by typing:
iptables -A INPUT 1 -s [ip-address] -j DROP/REJECT2. Restart the service with:
service iptables restart3. Save the new rule:
service iptables save4. Restart your web services. For example, if you run an Apache web server, type:
sudo systemctl restart apache2The system is now configured to reject the traffic from the suspicious IP address.
Conclusion
This article introduced you to DDoS attacks and provided methods to identify them. Furthermore, it showed some quick response tips to help you fight the ongoing DDoS attack.
Properly securing a server minimizes the chances of a damaging DDoS attack. Read 21 Security Tips to Secure Your Server to learn more about server security.